The purpose of this article is not to show how to hack email accounts, but to demonstrate the power of Hydra combined with a strong wordlist.
Hydra is a tool that makes cracking protocols such as pop3, ftp and telnet relatively easy. In my example, I will be cracking an email account (my own). Hydra uses brute force, so you HAVE to have the word in your wordlist in order to hack the email.
Wordlist Post
I’ll be hacking a pop3 email account but you can use other protocols, such as: TELNET, FTP, FIREBIRD, HTTP-GET, HTTP-HEAD, HTTPS-GET, HTTPS-HEAD, HTTP-PROXY, HTTP-PROXY-NTLM, HTTP-FORM-GET, HTTP-FORM-POST, MYSQL, POSTGRES, POP3-NTLM, IMAP, IMAP-NTLM, NCP, NNTP, SMTP-AUTH, SMTP-AUTH-NTLM, SSH2, SNMP, CVS, VNC, POP3, VMWARE AUTH.
1. Open Hydra typing “xhydra” or go through menu.
2. On the Target tab, enter the target, the port, the protocol and check the options like below:
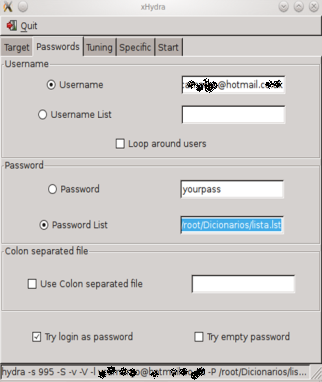
3. On the Passwords tab, enter the username (the email account you want to hack check password strength). Check the “Password List” button (then choose the path to your password list), “try login as password” and empty password options.
4. On the Tuning tab, you can select the number of tasks and the timeout time. I left mine at default, but you may need to edit these if you have trouble with the attack.
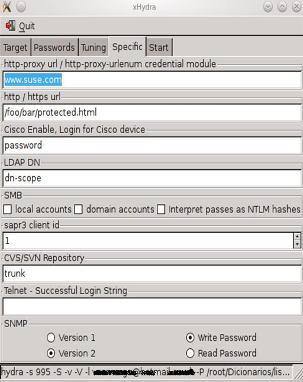
5. Leave “Specific” tab like that.
6. On the Start tab, click on Start and watch the output. Once it finds a password match (if it finds one), it will be highlighted in black.
As you can see, it is quite easy to perform a brute force attack using Hydra.
Remember, don’t run these attacks on anything other than your own servers.





how to download the software ??
ReplyDelete